For iPhone users leveraging the Microsoft 365 suite, especially those using the Outlook mobile app, navigating synchronization limitations can often feel like a tricky endeavor. This article delves into these challenges, particularly focusing on contact synchronization limitations, and offers practical workarounds to enhance productivity. One-Way Contact Synchronization The Outlook mobile …
Windows 10 End of Life
EXTENDED SUPPORT ENDS OCTOBER 14th, 2025 Microsoft has announced that support for Windows 10 will end on October 14, 2025. This means that after this date, Microsoft will no longer provide security updates, bug fixes, or technical support for devices running Windows 10. While this doesn’t mean that Windows 10 …
Unleashing Creativity and Productivity of Microsoft 365 Copilot
In the dynamic realm of productivity tools, Microsoft 365 Copilot emerges as a transformative addition, seamlessly integrated into Microsoft 365 apps to enhance your work experience. Writing Enhancement: Copilot acts as your AI-powered writing assistant, refining phrasing, correcting grammar, and sparking creativity across various tasks. Priority Access: Subscribing to Microsoft …
Breach Prevention Platform
At Glassen, we utilize the Breach Prevention Platform (BPP) to help keep our clients protected. The BPP mitigates Human Security risks, helps identify Cybersecurity risks, and meets many Compliance requirements which call for a “Reasonable Cybersecurity Program”. This continuous security program is the all-in-one solution built to establish ongoing security …
Employee Spotlight
Gage Eakins – Service Desk Lead Q: What is your job title and how long have you been with the company? A: I’m a Service Desk Lead and have worked at Glassen since 2023. Q: What is it like working at Glassen? A: Glassen is a close-knit group of enthusiastic …
External Vulnerability Scanning
In today’s digital landscape, cybersecurity is a critical concern. External vulnerability scanning is a proactive approach to identifying, assessing, and mitigating potential weaknesses in an organization’s external-facing infrastructure. It’s like conducting a security health checkup, looking for weak spots that hackers might exploit. The scanning process involves preparation, scanning, analysis, …
Elevating Communication: Azure Speech Services for Voice-Overs and Greetings in 3CX
We’ve begun to incorporate Azure Speech Services to produce polished and professional voice-overs and greetings within the 3CX VoIP Phone System. Through Azure’s Text-to-Speech technology, we’re able to convert your written prompts into sophisticated and lifelike speech, infusing a refined and welcoming tone into client interactions within our customers phone …
Employee Spotlight
Chris Wagner – Service Desk Technician Q: What is your job title and how long have you been with the company? A: I am an IT Technician and have been with the company since May of 2019. Q: What is it like working at Glassen? A: Working at Glassen is …
Employee Spotlight
Chad Klamer – Field Technician Q: What is your job title and how long have you been with the company? A: I am a Field Technician and have been with Glassen Technology Services for 7 years. Q: What is it like working at Glassen? A: Some days it can feel …
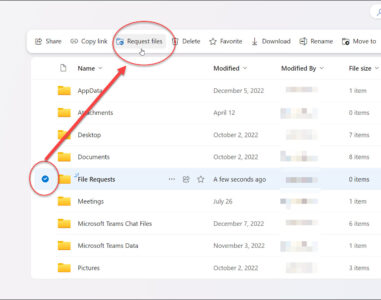
Requesting Files in OneDrive
Introduction In today’s connected world, working together is important. Whether you’re sharing documents, CAD drawings, graphic design files, or videos, sharing and collecting files easily is a must. Microsoft OneDrive, a cloud storage, and file-sharing tool, has a useful feature called “File Requests” that makes getting files from others simpler. …